Threat Intelligence and The Pyramid of Pain

There is great interest among security technology and service providers about the intersection of global threat intelligence with local observations in the network. While there is certainly cause for excitement, it’s worth pausing to ask the question “Is Threat Intelligence being used effectively?”

Applied Sciences, Free Full-Text

RVAs3c: David Bianco: Pyramid of Pain: Intel-Driven Detection/Response to Increase Adversary's Cost

Cisco Security Alignment to the Pyramid of Pain: Part 1 The Overview

APNIC on X: Cyber threat intelligence sharing – ascending the pyramid of pain, one of our #top3 #cybersecurity posts for 2016 / X
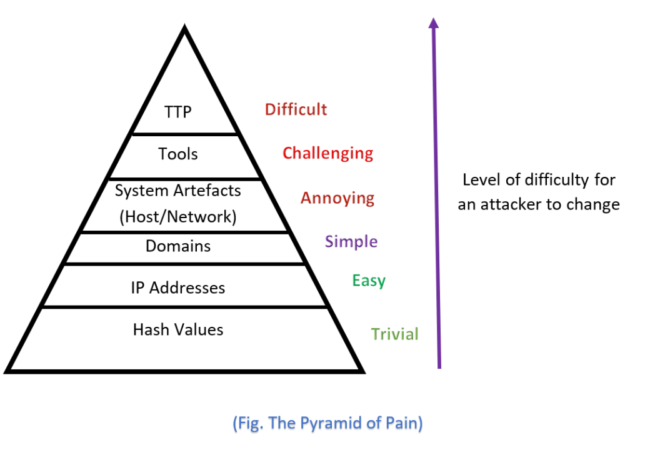
The Cyber Security Pyramid of Pain - Defending Against Attacks

Mapping zveloCTI to the Pyramid of Pain IOCs for IR & Threat Hunting

Thomas Roccia 🤘 on X: Visualizing #cybersecurity concepts can be a great way to learn more about specific tools, methodologies, and techniques! Here is a thread that shows 6 useful infographics on

The Pyramid of Pain and Cyber Threat Intelligence
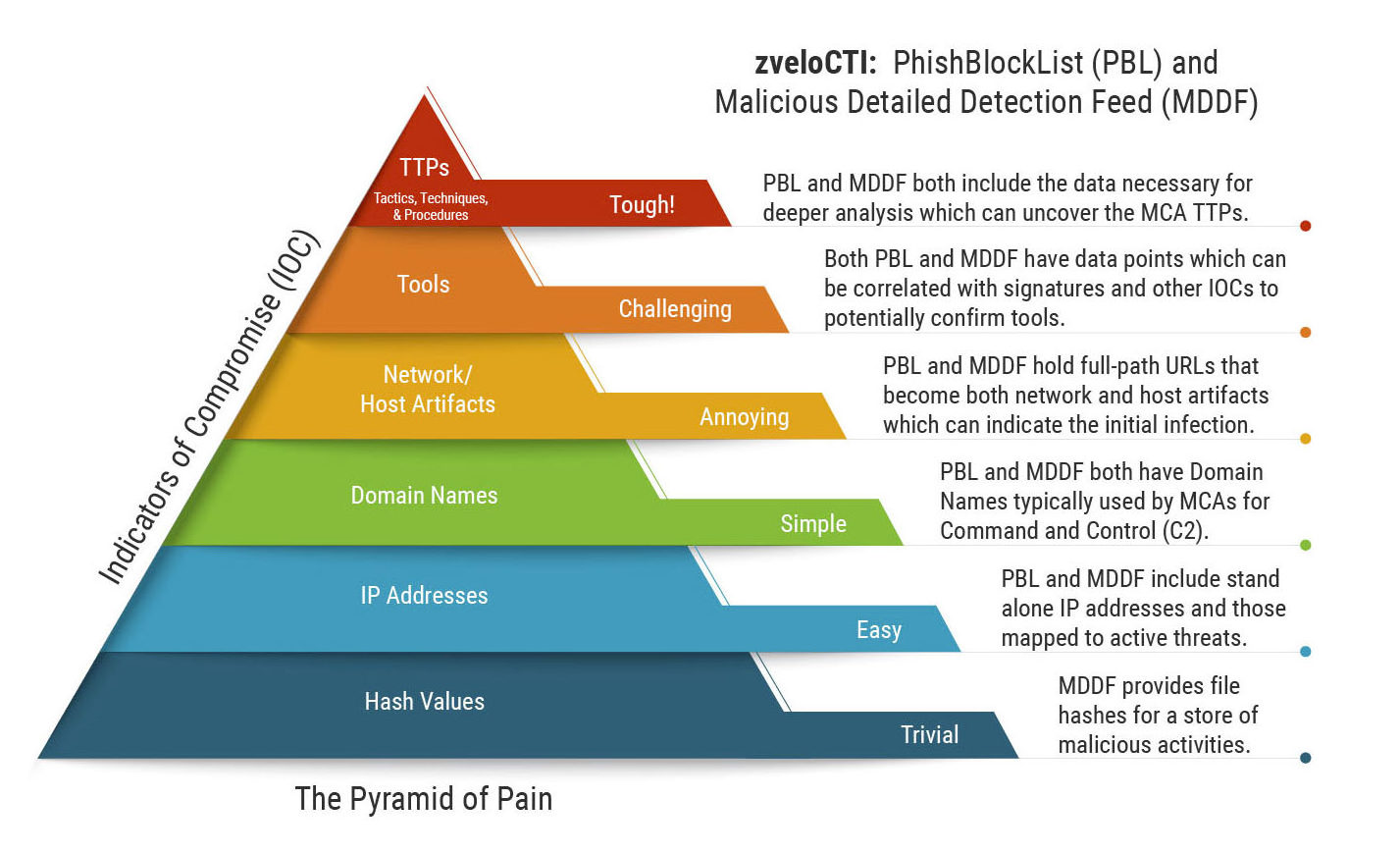
Mapping zveloCTI to the Pyramid of Pain IOCs for IR & Threat Hunting
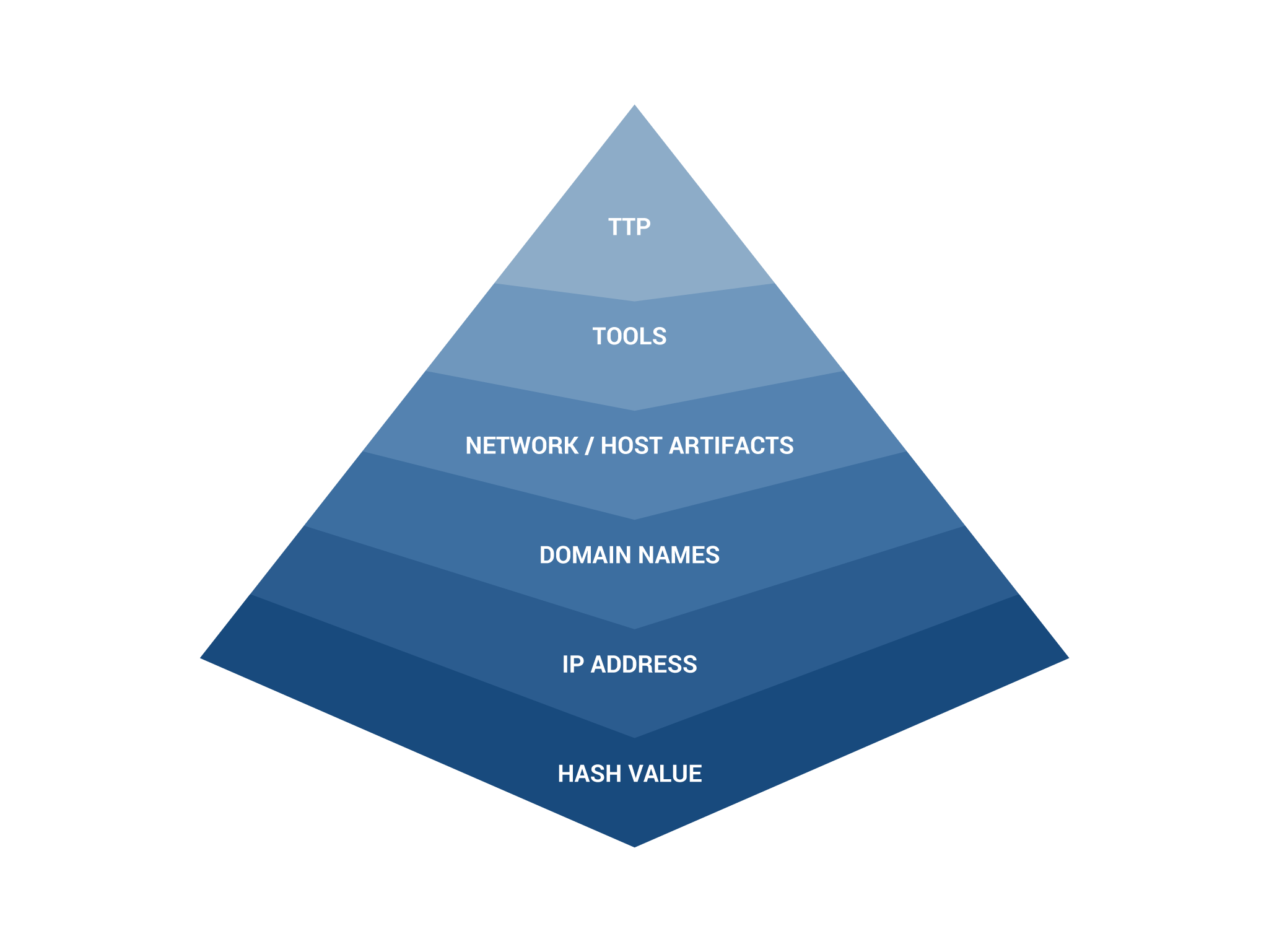
Threat Hunting Architecture - Securonix

Rethinking The Pyramid Of Pain In The Atomized Network
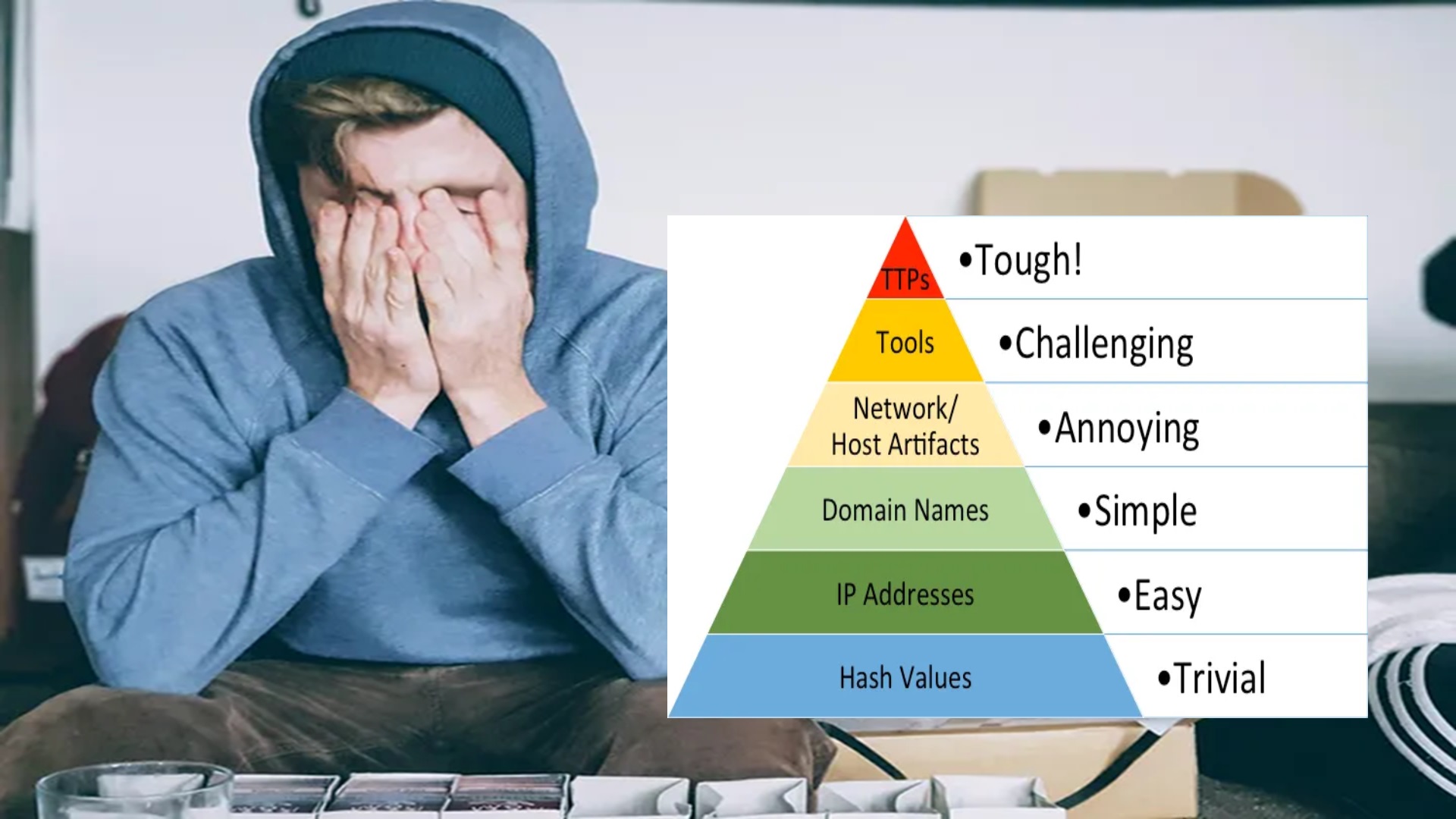
Elevate Your Threat Detections Using the Almighty Pyramid of Pain - Kraven Security









